Aperture Governance Studio has developed a series of comprehensive and highly configurable data management tools within their class-leading software. It provides organizations with complete control over their Data Governance, Migration and Quality projects.
Aperture Governance Studio is either hosted in the Azure cloud or deployed to the client’s cloud or on-premise environment. It has been designed with cross-platform functionality in mind, meaning you can access and use the software tools from any device.
Aperture Governance Studio maintains a 24-month roadmap of new functionality and enhancements to the software. This roadmap is reviewed regularly and is prioritised based on the needs of our clients. The latest roadmap can be shared on request.
Our software is developed following the Agile methodology. We release every 6-12 weeks with a global update to all clients. These updates feature new functionality, patches, and hotfixes.
Any identified security issues raised as ‘Critical’ or ‘High’ are fixed and all environments patched as soon as possible. ‘Medium’ priority issues are fixed and patched during the normal release cycle.
Every release is thoroughly tested internally using both automated and manual testing methods.
Aperture Governance Studio is developed and supported entirely from the UK.
Aperture Governance Studio are an ISO27001 certified organisation (BSI Certificate number 715111) for the following scope:
The provision of a unique software tool that allows organisations to manage their data quality, governance and migration programmes and the processing of data as part of consultancy services for data fundamentals (quality, governance, migration, et al.), both at client sites and at our site. This is in accordance with the ISMS Statement of Applicability, Version 1.3, dated 1st August 2022.
Aperture Governance Studio has Information Security Management policies and standards that can be provided on request. We routinely process Personally Identifiable Information, sensitive data, and classified data across a variety of sectors.
We are fully compliant with all applicable legislation and our ISMS is audited both internally and externally.
Aperture Governance Studio either has Data Processing and Non-Disclosure Agreements or G-Cloud contracts in place with all clients, which detail the Controller/Processor relationship and legal basis for processing.
Single sign-on for Azure Active Directory is available via the OAUTH method. Other SSO solutions can be supported on request.
Aperture Governance Studio can manage users and authentication internally. When users are added to the tool a time-limited link is sent to the user’s email address, which, when followed, requires them to set up a password in line with Aperture Governance Studio’s Password Policy. User permissions are defined per the RBAC in the next section.
Passwords are stored in the database using bcrypt with salt.
Roles can be set up within Aperture Governance Studio, expanding or limiting functionality available for users. Roles are linked to groups of configurable permissions, and any combination of permissions can be applied to a user. Over 250 individual permissions control all areas of the software.
Users can also be added to Roles and Teams to quickly assign common permission sets and configure workflow notifications.
The process document for configuring permissions and roles is available on request and is part of the technical administration training.
All actions in the software are logged in the audit tables. Key activities (logins, user creation etc) are sent to a central logging tool to ensure logs remain available in the event an environment has become inaccessible. Audit tables can be made available to clients for onward consumption downstream.
Data moving between the layers of the software is protected in transit via HTTPS/TLS 1.2 using a 2048 bit key.
Data at rest in the database is encrypted using 256-bit AES.
Backups are taken daily, each evening, and can be restored in a Disaster Recovery situation usually within 4 hours. All backups are done in full and are protected by means of encryption.
Backup media is regularly tested to ensure that they can be relied upon for emergency use when necessary, and is combined with a test of the restoration procedures and checked against the Recovery Point and Recovery Time objectives.
Our current RPO is 24 hours; RTO is 8 hours.
The retention period for data is determined with the client.
Aperture Governance Studio use continuous third-party penetration testing against all releases. This testing is conducted by an appropriate organisation with CREST Registered Penetration Testers. Test reports are available on request.
Our current security partner is Precursor Security.
All Aperture Governance Studio Azure environments are protected by Microsoft Defender. Definitions are updated, and Operating System updates are applied, daily.
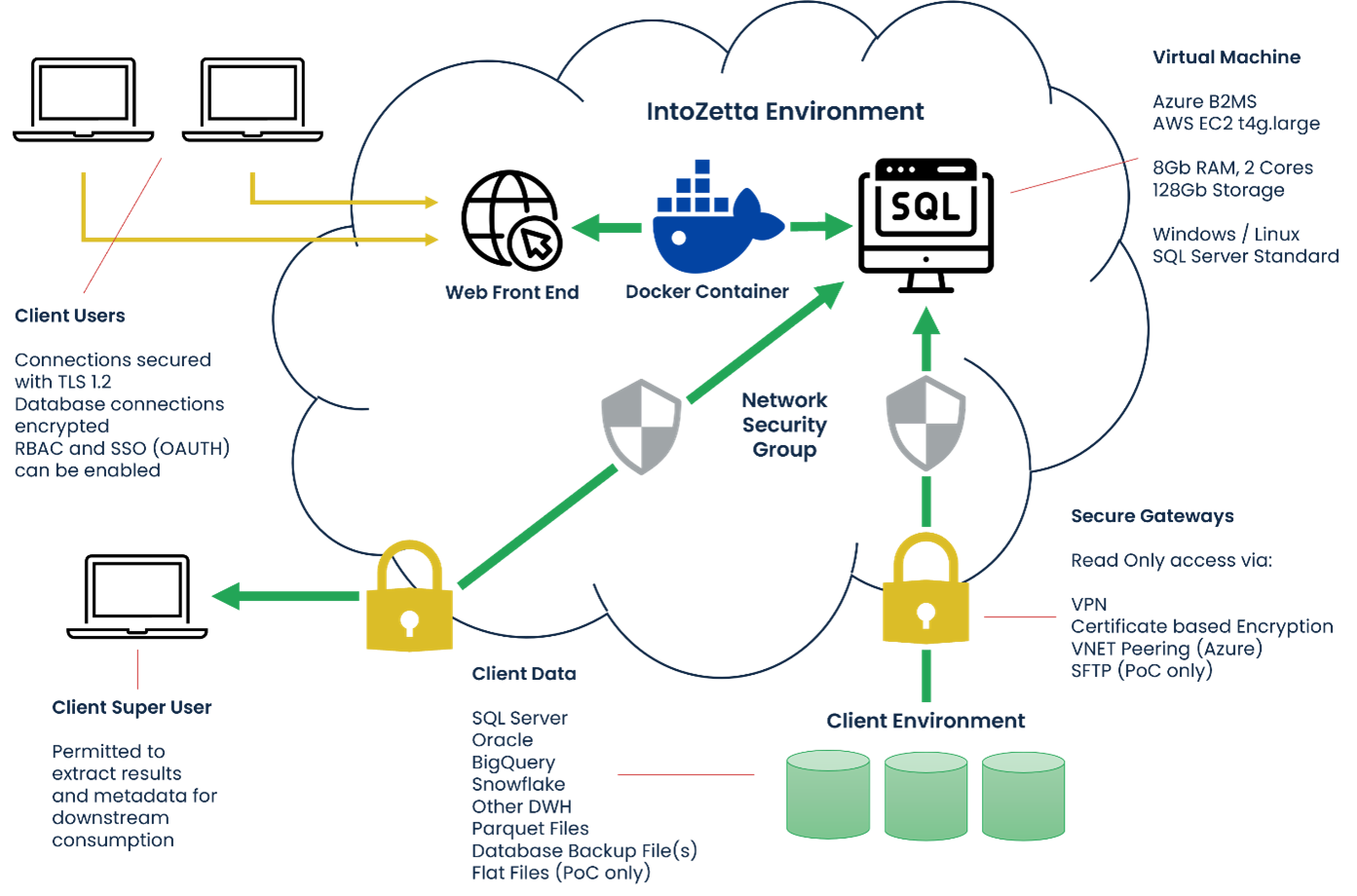
Aperture Governance Studio hosted instances are provided as Software-as-a-Service using Microsoft Azure.
As default, an Azure B2MS Virtual Machine runs both the SQL Server database and the Docker containers providing the front and back ends. Where required, a more powerful Virtual Machine can be deployed (additional costs may apply), but this standard set up is sufficient for almost all organisations.
Per the Architecture diagram in the Overview section, there are several options for securely connecting to data from the Aperture Governance Studio environment, which are detailed in the Connectivity section of this document.
Aperture Governance Studio actively manage each client environment, and every environment is unique per client. Any updates and patches are applied automatically, and all support can be provided remotely.
A client cloud implementation is architecturally identical to a SaaS set up. The environment can be set up in Azure, AWS or Google Cloud.
This set up has the advantage that client data never leaves the client environment and Aperture Governance Studio can still provide remote support and updates, provided the required access is provided.
This set up does require the client to take ownership of all environment costs, security and anti-malware protection and maintenance activity, including backup and recovery and performance management.
For non-cloud clients, it is possible to install Aperture Governance Studio onto physical servers within a client’s premises.
For this method, Aperture Governance Studio will supply encrypted packages containing the software, which must be installed by the clients’ system administrators. Updated packages will then be supplied periodically for the client to install.
Aperture Governance Studio requires a set up very similar to the cloud set up, particularly the ability to unpack and execute Docker containers.
As above, the client assumes all responsibility for the environment in this set up. Remote support can only be provided in the event the client configures the appropriate tools for external access such as Citrix. On-site support can be provided at 72 hours’ notice and at additional cost.
Further information on the requirements and method of installation on-premises are available on request.
The preferred method of encrypting data between client and an Aperture Governance Studio hosted instance is a VPN. Where the Aperture Governance Studio instance is hosted in Azure, an IPSec site to site VPN is created between the network hosting the software and the network hosting the source data. Access to specific sources in scope for data management can then be controlled at the network level.
The process for setting up the VPN typically involves an Aperture Governance Studio technical engineer and a client network engineer/3rd party VPN provider. Providing there are no connection issues, and the appropriate information is available, the connection can normally be made in less than a day.
The process steps are as follows:
Certificates based encryption involves the installation and sharing of certificates between connection devices. Encryption is applied at the device level.
Certificates are obtained from a trusted Certificate Authority (CA). The certificate is imported into the certificate store for the Server hosting the Aperture Governance Studio database and the SQL server instance.
The client server is configured to allow certificate based encrypted connections to the database.
A linked server connection is made from the Aperture Governance Studio database to the client data source identified as in scope for data management. The encrypted connection is validated by reviewing the SQL server connection tables.
VNET peering is an option within the Azure platform to connect virtual networks. Resources on one network can reach other resources on a separate network, with the networks materialising as one for connectivity.
Traffic is routed through the Microsoft private network. Traffic can flow cross subscription between resource groups, providing seamless connectivity to the source data.
SFTP transfers may only be used during the Proof-of-Concept phase. SFTP uses the SSH (Secure Shell) protocol to encrypt all data in transit between the client and Aperture Governance Studio.
Aperture Governance Studio can set up an SFTP file server and provide the credentials to the client. Files can then be dropped into the location and picked up by the Aperture Governance Studio consultant working on the account.
Aperture Governance Studio does not recommend connecting directly to source systems. In-scope data should be staged to remove the risk of unexpected load on source systems when Aperture Governance Studio is processing.
Access to the linked data is agreed with the client and is only required for consultant(s) working with the client and the application itself.
The software permits connections to multiple data sources.
What follows are the most common connections available, although Aperture Governance Studio can be configured to interface with other technologies not listed here.
The most common and straight-forward solution for data staging is a SQL server database or managed instance.
The user access is controlled by the client and only in-scope data is required to be stored here. A linked server connection is made by Aperture Governance Studio using the credentials provided by the client, which allows the data quality batch and profiling jobs to run.
For data staged in an Oracle database, the Oracle driver for the connection is installed. In the same way as above, a linked server connection is made with the Oracle driver.
A DSN is created containing the database login information. The DSN is referred to in the linked server and the connection is made.
To connect to BigQuery, the Simba ODBC driver is downloaded and installed to the Aperture Governance Studio server hosting the client’s instance. A system DSN is created referencing the Simba driver.
On the client side a service account is created and the service account is given access to the data in scope for the quality assessment. A BigQuery API is created for the user, and a JSON key file is generated.
The JSON key file is securely shared with Aperture Governance Studio, which is stored on the virtual machine hosting the Aperture Governance Studio instance. The service authentication in the DSN is updated with the key file path.
The linked server is created referencing the BigQuery DSN and the quality rules are written using open query to assess data stored in the BigQuery instance.
For data staged in Snowflake, the Snowflake ODBC driver is installed on the virtual machine hosting the Aperture Governance Studio instance. A DSN is created on the host using the ODBC driver. The additional connection parameters are adjusted.
A user is created on the Snowflake side for access to the warehouse. A default warehouse is assigned. Authentication can also be completed using a JWT which is provided and the Authenticator parameter is set to SNOWFLAKE_JWT.
Once the DSN is set up it is referenced in the linked server connection; Aperture Governance Studio can then run queries against accessible warehouses.
Aperture Governance Studio can work with and connect to a variety of technologies. Where data warehouses or other data stores are not listed in this document, Aperture Governance Studio can configure connectors to ensure data can be accessed by the tool and consultants working on data management with you.
Parquet is an open source file format that stores data alongside its metadata. The data is also compressed to keep the file sizes small.
The data from these files, once unpacked, are staged in a SQL Server instance within the Aperture Governance Studio environment. Where total file size exceeds 128Gb then additional costs may apply.
Database backup files from a SQL server are a good alternative to flat files such as CSVs. The database backup file retains meta data which is imported into Aperture Governance Studio. Database backup files can be quicker to implement than flat files which normally contain format conflicts.
A .BAK file is extracted from the source database and provided to Aperture Governance Studio. This will be done using an SFTP which Aperture Governance Studio can set up and provide the credentials for. The .BAK file is retrieved by Aperture Governance Studio and restored to a staging database on the same server as the Aperture Governance Studio instance. This means no queries are run between networks.
These files, once unpacked, are staged in a SQL Server instance within the Aperture Governance Studio environment. Where total file size exceeds 128Gb then additional costs may apply.
Flat files may only be used during the Proof-of-Concept phase. The client provides Aperture Governance Studio with a set of tables and/or views of in scope data in fixed-width or delimited files. It is preferable that such files contain headers and, where available, a data dictionary or schema.
These files, once unpacked, are staged in a SQL Server instance within the Aperture Governance Studio environment. Where total file size exceeds 128Gb then additional costs may apply.
External access to the database directly is restricted by IP address on the default 1433 port. All passwords are set following Aperture Governance Studio’s password policy.
Access is granted to Aperture Governance Studio’s results, metadata and audit tables. System tables are not accessible by clients.
Client users who are sufficiently competent in SQL and are approved by the client and Aperture Governance Studio may be granted access to populate data directly into the back end of the software. However, issues with data uploaded in this way are not covered by Aperture Governance Studio’s support policy.
Data from the tables mentioned above may be extracted for client use outside of the software.
Should the client not wish to perform that extraction themselves, this can be done by Aperture Governance Studio consultants as part of a service package.
Connections can be made from Aperture Governance Studio to 3rd party reporting tools such as PowerBI, Qlik and Tableau.
Aperture Governance Studio offers a range of charts and analytics to monitor trends across the client data environment. In some instances, clients will wish to augment other metrics and reports with data management analytics.
Aperture Governance Studio can make reporting data available to third party reporting tools and will create a database user with read only access to reporting information. This can then be consumed by a 3rd party reporting tool and presented alongside existing reports such as a monthly update dashboard/pack.
As well as providing data to third party reporting system, Aperture Governance Studio offers the integration of 3rd party reporting tools into the suite itself. This means custom reports can be created in a tool like PowerBI and present data within Aperture Governance Studio, alongside other metrics within the tool.
The embedded reports section uses iframes to embed links to hosted reports and each frame is tabbed so multiple reports can be created and stored within the tool. This means your custom data reports are stored and used in the same space as your data management modules for maximum visibility.